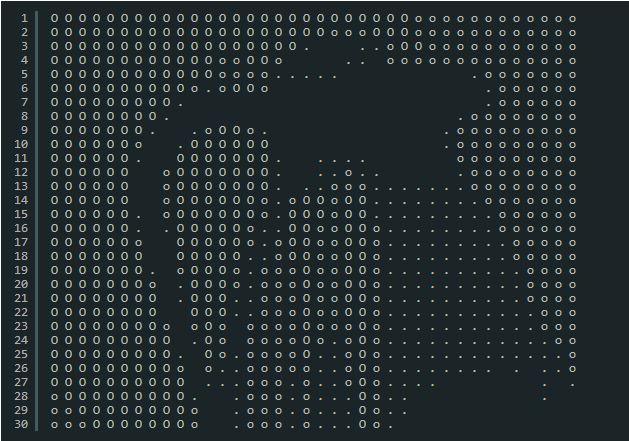
Core Security has published several critical issues with 16 D-Link IP camera models. This includes a hardcoded password — “?*” — which provides administrative access to the devices giving attackers to access live RTSP video stream from the camera. The bulletin contains details on five vulnerabilities discovered in the firmware deployed on various D-Link IP cameras. The vulnerabilities can be exploited remotely by an attacker bypassing allowing direct access to Real Time Streaming (RTSP) video stream, execute commands on the devices via HTTP and giving access to a black-and-white ASCII video stream. D-Link released updated firmware Thursday to address the vulnerabilities.
Multiple vulnerabilities were also identifying in two different models of Vivotek IP cameras. Vivotek cameras store wireless keys and third-party credentials in clear text. This allows attackers to obtain sensitive information including FTP access, shared folder credentials, and wireless access point keys. The vulnerabilities also include the ability to trigger a remote buffer overflow for arbitrary code execution on a device. Core Security has made six failed attempts in alerting Vivotek to the vulnerabilities however no official answer has been received. This has led the security company to publish the complete vulnerability details alerting end users about the flaws in Vivotek’s firmware.
In early March, warnings were made about the flaws some Foscam IP cameras which allow attackers to remotely bypass normal authenticatication mechanisms on the devices. as well as to steal the authentication credentials stored on the devices. Following the alert, Foscam released a firmware updated but according to Qualys, which discovered the vulnerabilities, 99% of the vulnerable devices are still running old versions of the firmware.
“Security patches for hardware devices like routers, printers and cameras are often overlooked,” says Paul Ducklin, Sophos head of technology. “Always-on devices like routers and cameras are typically part of your security infrastructure, so a compromise on one of them could facilitate the compromise of your whole network”