You can access the law here [PDF].
The law is expected to curb cybercrimes and computer related offences to enable timely and effective detection, prohibition, prevention, response, investigation and prosecution of computer and cybercrime.
The National Computer and Cybercrimes Co-ordination Committee
The law creates the National Computer and Cybercrimes Co-ordination Committee. The role of this committee includes advising the Government on security related aspects touching on matters relating to blockchain technology, critical infrastructure, mobile money and trust account.
Blockchain and Cryptocurrency
Blockchain technology under this law is defined as a digitized, decentralized, public ledger of all crypto currency transactions.
The law does not talk of anything on the use of the technology for cryptocurrency or other distributed ledger uses other than that, the new committee will advice on this.
Critical Infrastructure
“Critical information infrastructure system or data” means an information system, program or data that supports or performs a function with respect to a national critical information infrastructure;
The Director of the New National Computer and Cybercrimes Co-ordination Committee is expected to designate certain systems as critical infrastructure. These mean the processes, systems, facilities, technologies, networks, assets and services essentials to the health, safety, security or economic wellbeing of Kenya.
Cybersquatting and Domain Name
Cybersquatting simply put is, taking someone else’s domain name knowingly for a wrongful purpose. For example, registering the domain name google.or.ke and you are definitely not Google. This is now expressly recognized in Kenyan law and it is laudable.
Mobile Money
“Mobile money” means electronic transfer of funds between banks or accounts’ deposit or withdrawal of funds or payment of bills by mobile phone.
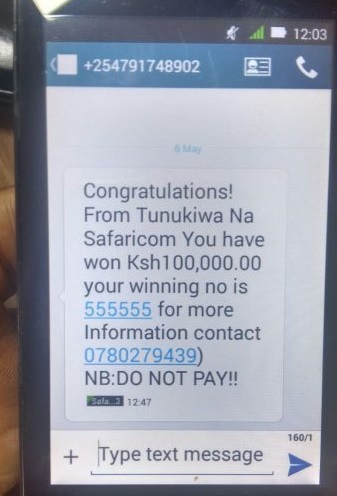
If you’re in Kenya, you’ve probably used a mobile money service and more likely than not, have sent money to the wrong number. You call the person (remembering we’re a 80% Christian nation) hoping that morality and ethics shall prevail, asking the guy to woishe send you the cash back. Even a part of it. We all know, that rarely happens. You ask the service provider to reverse the transaction they say, the money has already been withdrawn or that you need to report to the police.
The Act now makes it a crime for someone to intentionally hide or detain electronic payment delivered to the person in error and which ought to be delivered to another person.
Also, any person who, with intent to defraud, sends electronic messages, instructions, subscribes any electronic messages or instructions commits an offence.
Data Protection
The law allows for information sharing between owners of critical infrastructure. However, it limits the sharing of health status information without consent of the data subject which is a fundamental data protection principle.
Employee Responsibility
As most of our readers are in the tech industry and their businesses are fundamentally driven by computer systems, this provision is of interest. Employees are expected to relinquish all codes and access rights to their employer’s computer network or system immediately upon termination of employment.
Criminal Offences
Most of the offences in the law had already been in place under the current Kenya Information and Communications Act (KICA). These include unauthorized access, unauthorized interference, accessing computer systems with intent, Unauthorized disclosure of password or access codes
Of the legacy offences, what is fundamentally different is that the penalties now are much higher from 5 to 20 million or imprisonment of around five (5) years. Normally, the idea behind criminal law such as this, is to act as a deterrent to stop people from committing such offence. That’s why the penalties are as punitive.
The penalties for the legacy offences are even higher for interfering with systems that contain highly sensitive and classified information such as those for security, defense and critical infrastructure.
Problematic Provisions
Several groups have come up against the new law; these include civil society organizations such as Article 19, the Media Council of Kenya, the Public Interest Litigation arm of the law society and the Bloggers Association of Kenya.
One of the common concerns are the offences relating to fake news. The law provides that “A person who knowingly publishes information that is false in print, broadcast, data or over a computer system, that is calculated or results in panic, chaos, or violence among citizens of the Republic, or which is likely to discredit the reputation of a person commits an offence and shall on conviction, be liable to a fine not exceeding five million shillings or to imprisonment for a term not exceeding ten years, or both.”
A famous court decision of Republic v Geoffrey Andare had the impact of declaring section 29 of the Communications Act (KICA) unconstitutional because the section was vague and too broad. In my personal opinion, this is a problematic section and it doesn’t meet the Constitutional threshold of laws.
Another section is that of cyber harassment where one communicates to another with the effect of causing apprehension or causing detrimental effect. As a woman actively online and in the tech community, I know of so many people, ladies especially, but also men, who have been harassed online because of the false perception of online anonymity. It is a problem that needs to be addressed.
Another key issue is the investigative procedures of the law and the powers that the law gives to the police. It talks of an “authorised person” being an officer in a law enforcement agency or a cybersecurity expert designated by the Cabinet Secretary of Interior. It would be interesting to see who these “experts” shall be.
Generally, we all know that we need a law to protect users in the internet and tech age. How the law was largely framed was identifying the problem and then backtracking to put it into words. All lawyers know that the translation matrix from English to Legalese and vice versa is not a simple task.
Also, if I may, most of the people complaining about this law are people who did not contribute to the law-making process and did not give any thoughts during the extensive public participation process from 2016. Granted, a number of aggrieved stakeholders did, myself included, but most Kenyans, truth be told, did not.
In my opinion, the law is timely and is needed. Some sections are problematic and need to be corrected. I’m waiting to see how it all plays out.