Recent cyberattacks waged on Kenya’s online infrastructure have left various Government and privately owned services crippled as many citizens question the country’s level of preparedness against prevailing cyber threats. The group claiming responsibility is Anonymous Sudan.
Who Are Anonymous Sudan?
The hacktivist group based in Sudan has been hitting headlines in a wave of attacks against various Governments around the world. The group usually targets critical sectors in the country including education, government, finance, healthcare and aviation.
The attacks appear motivated by religion and politics with the first message posted on their telegram channel being, “We will attack any country with Cyber attacks against those who oppose Sudan”. Sticking to their words, their recent victim in their campaign is Kenya.
The pro-Russian hacktivist’s weapon of choice is Distributed Denial of Service (DDoS) attacks on a state’s infrastructure. This form of cyber attack aims at disrupting a service or network rendering it inaccessible to its normal users. To achieve this, an attacker floods the service or network with internet traffic.
In what has been a “busy” year for the group, Anonymous Sudan has targeted mostly Western countries with their first attack being on Sweden and Denmark back in January. This was in retaliation to Rasmus Paludan (who is a duo citizen of the two countries) burning the Quran.
The group has continued to wage cyber warfare on other organizations in other countries including France, Germany, Israel, India, the U.K, and the U.S.A.
Recently, the group has started extorting its victims in order to stop the attacks. Notably, the group demanded $1 million from Microsoft to stop their DDoS attacks on Microsoft’s key services including Outlook, and Azure. This was a third of what the cyber criminals had demanded from Scandinavian Airlines back in May.
Russian Hackers?
Despite their name, security researchers believe that Anonymous Sudan is a Russian Hacking group. Researchers from Flashpoint point to the group’s affiliation with Killnet, a Russian hacktivist collective formed around March last year. In the report, Flashpoint Intel Team says, “Evidence also suggests that Anonymous Sudan are likely state-sponsored Russian actors masquerading as Sudanese actors with Islamist motivations, as cover for their actions against Western (or Western-aligned) entities.”
The researchers add, “Despite obfuscations on official Anonymous Sudan channels as to their identity and affiliations, the employment of social media or public facing accounts under the “hacktivist” banner is consistent with previous tactics, techniques, and procedures employed by Russian state-sponsored adversaries.”
The group took over the pseudonym of the “Original Anonymous Sudan” which emerged in 2019 in response to the country’s ongoing economic and political challenges. According to security researchers at SocRadar, the original Anonymous Sudan group was engaged in pro-Ukraine and anti-Russia operations. “Unlike the newer Anonymous Sudan, it is also known that they were involved in anti-Russia and pro-Ukraine ops with Ghostsec as a member of OpSudan hacktivism,” the team points out.
According to CyberNews, the group only started using Arabic in their posts after researchers pointed out that the group identifying with an Islamic country posted mostly in Russian. To cover their tracks, the group deleted older posts and started using “school-taught” Arabic, adopting the Sudanese dialect only later.
Apart from the DDoS campaign targeting U.S organizations in response to the US Secretary of State, Anthony Blinken’s comments regarding potential US involvement in Sudan affairs, the group had not been vocal on issues directly affecting Sudan and its people.
That is, until now.
The DDoS Attack on Kenyan Infrastructure
This week the saw Anonymous Sudan group launch a new campaign targeting Kenyan infrastructure through a series of DDoS attacks. This was in response to what the group termed as Kenya’s interference and meddling in Sudanese affairs.
READ MORE: Anonymous Sudan Continues DDoS Attacks On Kenyan Infrastructure
The attacks targeted critical infrastructure including various Government agencies, higher education institutions, private companies, and media companies among other public organizations.
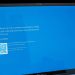
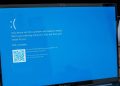
Multiple services including KPLC token systems, M-Pesa to bank services, and government services offered on the e-citizen platform were affected by the recent attacks. Various organizations have already released statements addressing the unavailability of their services citing “system hitches”.
Kenya Power and Lightning Company (KPLC) have already issued another statement confirming they have resolved the hitches.
The Kenyan e-citizen platform had been inaccessible for a while following the DDoS attacks. The ICT CS Eliud Owalo had confirmed that the e-citizen platform had been attacked. He further refuted claims by Anonymous Sudan that they compromised the system.
“It’s not strange because Cyber Attack is predominant the world over. We can not stop digitizing our records and digitalizing our services because we are risk averse. What we need to put in place is a risk mitigation framework which we are ready for anyway.” The CS said while speaking on Spice FM. The Government announced that E-Citizen services are back online.
Anonymous Sudan has further added that they have compromised key Government agencies including KRA and E-Citizen. According to a post in their telegram channel, the group intends to sell the data once done with the attacks.
The group has further “promised” more attacks today after Friday prayers.
Their demands:
The group posted two demands to the Kenyan government for the attacks to stop. In their telegram channel, the “hacktivists” say all attacks will cease if the government meets any of the two conditions:
Either an apology to Sudan issued by an Official from the Kenyan Government or $ 200,000 in bitcoin sent to their wallet.
Kenya’s Level Of Preparedness In the Face Of Cyberwarfare
There has been a rise in the frequency and sophistication of cyberattacks globally. The increasing development of emerging technologies including Artificial Intelligence, nanotechnology, blockchain and 5G, will further accelerate the complexity and severity of Cyber Warfare. The adaptation of these technologies in cyberspace will change the nature of wars.
Cyber warfare is unrestricted by borders and can cause more harm and as much damage as conventional warfare. What makes this form of warfare attractive to adversary nations is it’s relatively cheaper to deploy despite being highly impactful.
However, it is important to note that the recent DDoS attacks against our infrastructure is NOT cyberwarfare and does not even amount to cyber conflict. In an article, Gichuki Jonia, a former Cyber Command Operator at the Ministry of ICT says, “A full state-led operation would have all four effects conducted during a Computer Network Attack (CNA), i.e., disrupt, deny, degrade, and destroy. Thus, cyber is not just an enabler of war but also a strategic option in conflict. However, what we are observing is the maneuver of an adversary who lacks the capability to conduct CNA.”
Deterrence in the cyber domain relies more on resilience, deterring potential threat actors, and imposing costs rather than relying solely on political means. To harness the power of Nairobi’s offensive cyber capabilities, it’s imperative that corruption and political shenanigans come to a halt, allowing talent thread the needle and focus on capability development. This way, we can execute successful and impactful cyber operations against our adversaries via both DCO and OCO. As noted, acquiring the right talent is crucial since cyber initiatives should be a top priority within the national security agenda.
Gichuki Jonia (Chucks) on Countering The Current Distributed Denial of Service Cyber On-Slaughter Against GoK
ICT CS Eliud Owalo while on Spice FM added that the government was working towards building a “elaborate risk mitigation framework for sustainable digitalization”.
Recent cyber attacks on key agencies including the DDoS attacks by Anonymous Sudan and data breaches (KEBS and KAA data breaches) have revealed gaping holes in our cyber security systems and a lack of cyber awareness.
Read more: KEBS Suffers a Massive Data Breach
It is thus crucial for GoK to develop and implement cyber defensive strategies and practices to protect and strengthen our network and critical infrastructure.