A new ransomware variant, dubbed Boramae, has been identified by cybersecurity researchers, posing a significant threat to Windows-based systems.
First observed on March 4, Boramae employs advanced encryption techniques and exhibits sophisticated evasion strategies, making detection and removal particularly challenging.
Infection Mechanism and Ransom Demands
Upon infiltrating a victim’s system, Boramae encrypts files and appends a unique identifier along with the “boramae” extension to each filename.
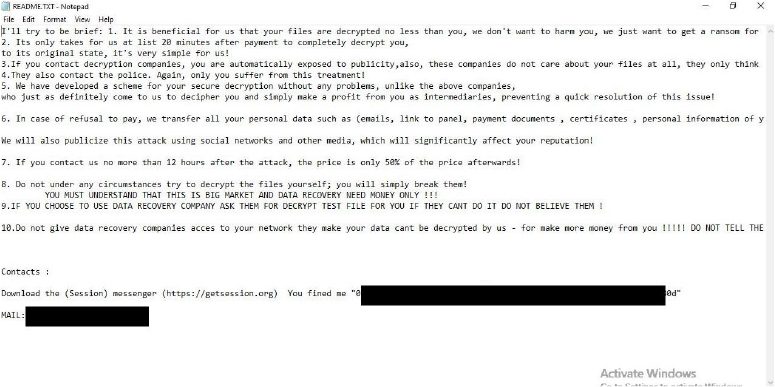
For instance, a file named “document.pdf” would be renamed to “document.pdf.{unique-ID}.boramae.” Subsequently, it generates a ransom note titled “README.TXT,” detailing instructions for file recovery.
The ransom note emphasizes urgency, offering a 50% reduction in the ransom if contact is made within twelve hours. It warns against manual decryption attempts, claiming they could permanently damage the files.
Additionally, it threatens to leak sensitive data, including financial records and employee information, to other hacker groups if the ransom is not paid.
Advanced Evasion and Persistence Tactics
The Boramae ransomware employs several sophisticated techniques to remain undetected and persist within infected Windows systems. These include:
- Modifying Registry Keys: Boramae alters specific entries in the Windows registry to ensure it launches automatically every time the system starts. This tactic allows the ransomware to maintain persistence, making it more challenging to remove.
- Process Injection Techniques: The ransomware injects its malicious code into legitimate processes running on the system. By doing so, it disguises its activities as part of normal system operations, helping it evade detection by security software.
- Utilizing Rootkits: Boramae employs rootkits (malicious tools designed to hide the presence of malware) to conceal its files and processes from both users and security programs. This concealment makes identifying and removing the ransomware more difficult.
- Pre-OS Boot Mechanisms: The ransomware can establish itself to run before the operating system fully loads, using techniques like bootkits. This early execution ensures it can activate before many security defenses are in place, further complicating detection and removal efforts.
- Obfuscated Files and Information: To avoid detection, Boramae obfuscates its code and related files, making it harder for security software to recognize and analyze the malware.
Recommendations to Mitigate Boramae Ransomware
- Maintain Up-to-Date Backups: Regularly back up critical files to multiple locations, including offline and cloud storage. Ensure backups are isolated from the main network to prevent ransomware from encrypting them.
- Exercise Caution with Emails: Avoid opening unsolicited email attachments or clicking on links from unknown sources. Verify the sender’s identity before interacting with any attachments.
- Keep Software and Systems Updated: Enable automatic updates for applications, operating systems, and security software to patch vulnerabilities that ransomware might exploit.
- Implement Strong Authentication Measures: Use strong, unique passwords and enable multi-factor authentication (MFA) to reduce the risk of unauthorized access.
- Educate and Train Employees: Foster a culture of cybersecurity by investing in employee training, ensuring that security is an integral part of your organization.
By adopting these proactive measures, organizations can enhance their defenses against Boramae ransomware and similar cyber threats.