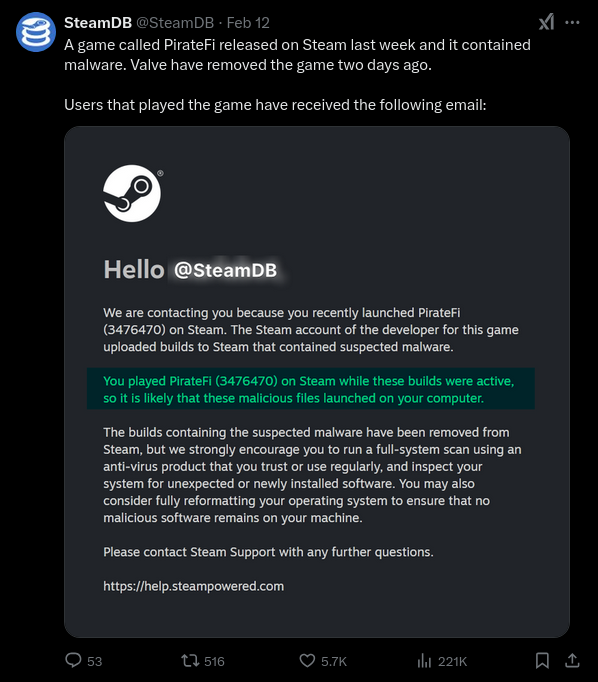
In a recent security incident, the free-to-play game PirateFi was removed from Valve’s Steam platform after it was discovered distributing the Vidar infostealing malware.
This malicious software targeted users’ sensitive information, including passwords, browser cookies, and cryptocurrency wallet details.
PirateFi was available on Steam from February 6th to February 12th, 2025, during which it was downloaded by approximately 1,500 users. The game contained Windows-based malware disguised as “Howard.exe,” which, upon launching, unpacked itself into the user’s /AppData/Temp/ directory.
This malware was designed to steal browser cookies, potentially granting attackers access to various online accounts. Several users reported compromised accounts, password changes, and unauthorized transactions.
Upon identifying the threat, Valve, the parent company of Steam, promptly removed PirateFi from the platform and issued warnings to potentially affected users. The company advised users to perform comprehensive system scans, uninstall unfamiliar software, and consider changing their passwords to prevent further unauthorized access.
Understanding Vidar Malware
Vidar is an infostealer malware that first appeared in late 2018. Operating as malware-as-a-service, it is designed to collect a wide range of sensitive data from infected systems, including:
- Passwords: Harvesting login credentials stored in browsers.
- Browser Cookies: Capturing session cookies to hijack active sessions.
- Cryptocurrency Wallets: Extracting keys and credentials for digital wallets.
- Two-Factor Authentication Data: Stealing information from authentication applications.
Additionally, Vidar can serve as a downloader for other malicious software, such as ransomware. Its operators offer it on underground forums, allowing other cybercriminals to deploy it in various campaigns.
The Vidar malware, concealed within the game’s executable file, was designed to extract a wide range of personal data from infected systems.
Security researchers noted that the developers of “PirateFi” uploaded multiple builds containing the malware, utilizing various obfuscation techniques and frequently changing command-and-control servers to evade detection.
Recommended Actions
For users who installed PirateFi or suspect a malware infection, here are some crucial steps to follow:
- Conduct a Full System Antivirus Scan: Utilize reputable antivirus software to detect and remove malicious programs.
- Remove Unfamiliar Applications: Uninstall software that was not intentionally installed.
- Change Passwords: Update passwords for all accounts, prioritizing financial and email services.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security to accounts where available.
- Monitor Financial Statements: Regularly review bank and credit card statements for unauthorized transactions.
To reduce the risk of encountering malicious software in the future, it’s essential to take proactive steps. Always download games from reputable developers and publishers. Also make a habit of reading user reviews to spot any potential issues.
Additionally, keep your antivirus and anti-malware programs up to date to defend against the latest threats. Be cautious with newly released games that have limited reviews, as they may not have been thoroughly vetted by the community.





























