A fraud intelligence team has identified a scam e-commerce network that is stealing peoples personal and financial data. The scammers are targeting unsuspecting individuals on Facebook using deceptive ads that usually have time limited offers. The team from Recorded Future noticed the scam campaign on the 17th of April this year and named it the “ERIAKOS” campaign.
The name ERIAKOS came from the usage of the Content Development Network (CDN) named oss[.]eriakos[.]com. These scam sites employed brand impersonation and advertising tactics to lure victims. A notable aspect of the scam sites used to steal Facebook users’ data is that they were only accessible via mobile devices.
“These fraudulent sites were accessible only through mobile devices and ad lures, a tactic aimed at evading automated detection systems,” Recorded Future wrote. The firm further noted that the network of websites was huge. Its intelligence team detected 608 fraudulent websites.
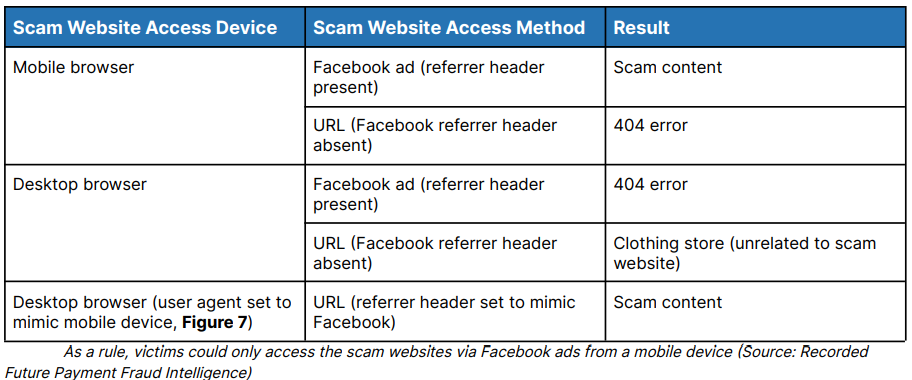
Ad lures targeting mobile Facebook users consisted of limited-time discounts to entice people into clicking on them. Recorded Future said as many as 100 Meta Ads related to a single scam website were served in a day. The counterfeit websites and ads have been found to mainly impersonate major online e-commerce platforms and power tools manufacturers. The sales offers were majorly for well-known brands.
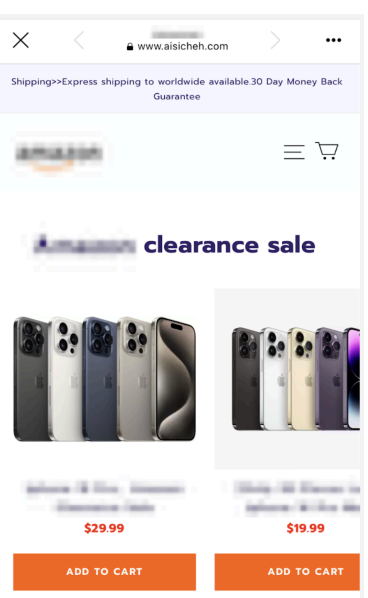
The use of advanced screening techniques in this campaign suggests a growing trend that might challenge current detection technologies. Targeting mobile devices meant the scam ads were likely to evade automated scanners.
READ: Netflix/Facebook Exchanged User Private Messages, Watch History in Scandalous Data Breach
The ERIAKOS scam campaign had key features, for example the ERIAKOS CDN. Secondly, all the domains for the 608 websites were registered with Alibaba Cloud Computing Ltd. Recorded Future also detected that two specific IP addresses (47[.]251[.]129[.]84 and 47[.]251[.]50[.]19) were consistently used. Lastly, the scam domains exhibited specific misconfigurations between their main domains and www subdomains. The use of Chinese PSPs to process payments was another feature.