Receiving an email from Google might feel safe, but it shouldn’t anymore. A new phishing campaign is leveraging a clever mix of Google OAuth abuse and DKIM replay attacks to deliver malicious emails that appear 100% legit, straight from Google’s own servers.
This phishing attempt is a highly convincing scheme that slips past security filters and lands directly in Gmail inboxes.
Hackers have found a way to exploit Google’s trusted infrastructure to send phishing emails that look like they’re coming from Google, and they really are. Here’s how it works.
Attack Process
1. Crafting the Bait
Attackers set up a legitimate-looking Google Workspace account and create a custom OAuth app. But instead of a real app name, they stuff phishing content (like fake alerts or threats) into the app’s name field.
2. Letting Google Do the Talking
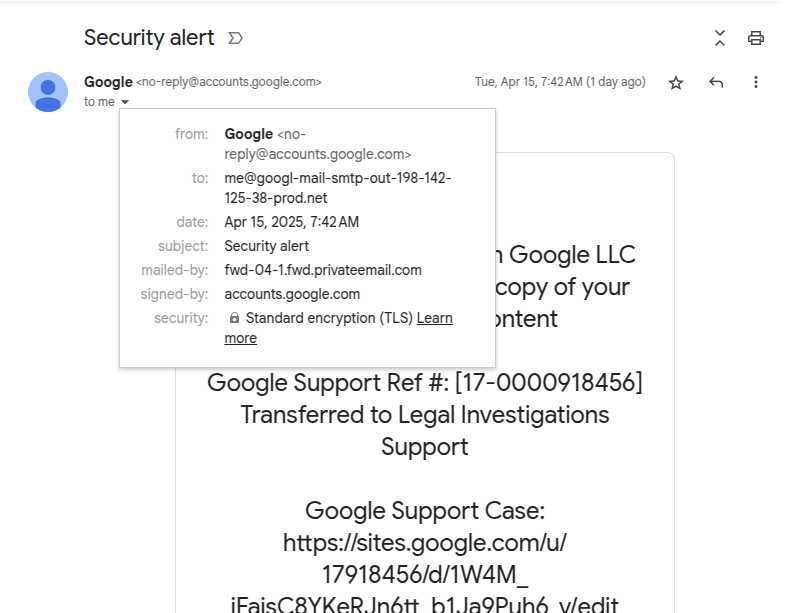
When users interact with the malicious OAuth app, Google, as part of its automated security features, sends a security alert email to the user. This email, ironically meant to notify about a new login, includes the app’s “name” (which is actually the phishing message).
3. Signed, Sealed, Delivered
Because the email is generated and sent by Google’s systems, it carries a valid DKIM signature, a digital signature that proves authenticity to email security systems.
4. Phishing Page on Google Sites
Clicking links in the phishing message leads users to a spoofed support page hosted on Google Sites, designed to look like a real Google support page, only it’s harvesting your credentials.
Why This Is Dangerous
- It bypasses spam filters: The email technically comes from Google’s servers, complete with all the proper authentication, so spam filters don’t flag it.
- It looks legit: Even savvy users might not think twice about an email from Google.
- It abuses trust: Hosting phishing pages on sites.google.com makes the entire attack feel even more real.
Google’s Response
Initially, Google said the behavior was “functioning as intended.” The emails were legitimate alerts triggered by user actions.
However, after cybersecurity experts like Ethereum Name Service developer Nick Johnson raised alarms, Google confirmed the abuse and started working on fixes to prevent this attack method.
How to Stay Safe
- Enable 2FA or passkeys: Add an extra layer of protection to your Google account. It’s your first line of defense if credentials are compromised.
- Review connected apps: Go to your Google Account → Security → Third-party access and revoke anything you don’t recognize.
- Always double-check URLs: Before clicking on links in emails, hover to preview them, or better yet, go directly to the site manually.
- Be skeptical of urgent language: “Your account is compromised!” and “Click here to recover!” are classic red flags.
- Report suspicious emails: Use Gmail’s “Report phishing” option to flag malicious emails.
This phishing campaign is a textbook example of attackers using trusted systems against us. When an email passes every security check and bears Google’s own digital signature, it’s certainly a tough one to spot.