

Pegasus has in the past been used to monitor special interest targets, specifically, journalists and human rights activists. NSO Group only sells pegasus to governments which raises the red flag as to who exactly was being monitored in Kenya.
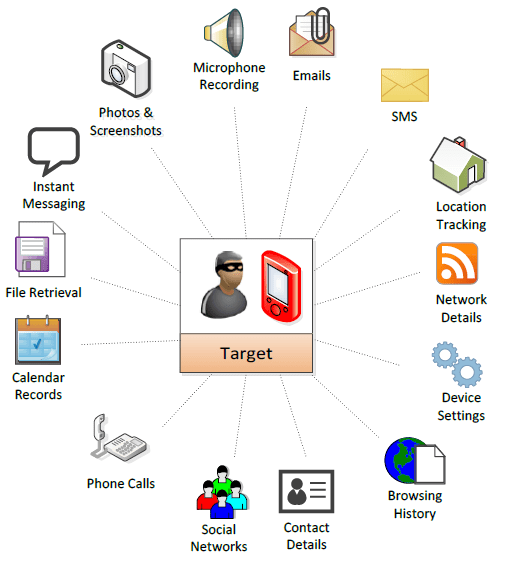
How the spyware works is rather simple to explain; a government operator of Pegasus creates a crafty link, sends it to the target and once clicked, the exploit link delivers a chain of zero-day exploits to penetrate security features on the phone and installs Pegasus without the user’s knowledge or permission. Pegasus has been observed to infect Android, iOS and BlackBerry operating systems.
Once Pegasus is installed, it sends back the private data, including passwords, contacts, calendar events, texts and even live voice calls from popular mobile messaging apps. Worse, the operator can even remotely turn on the phone’s camera and microphone.

Politically-Themed Spyware
Citizen Lab conducted a research that revealed Pegasus infections in 45 countries, including; Kenya, Morocco, Rwanda, South Africa, Togo, Uganda and Zambia, between August 2016 and August 2018. Narrowing everything down to Kenya, Citizen Lab identified GRANDLACS as the operator. GRANDLACS uses politically themed domains to influence targets to install the malware, for instance, GRANDLACS used the domain, politicalpress[.]org to spread the malware. This same operator has also been spotted in Rwanda, South Africa and Uganda.
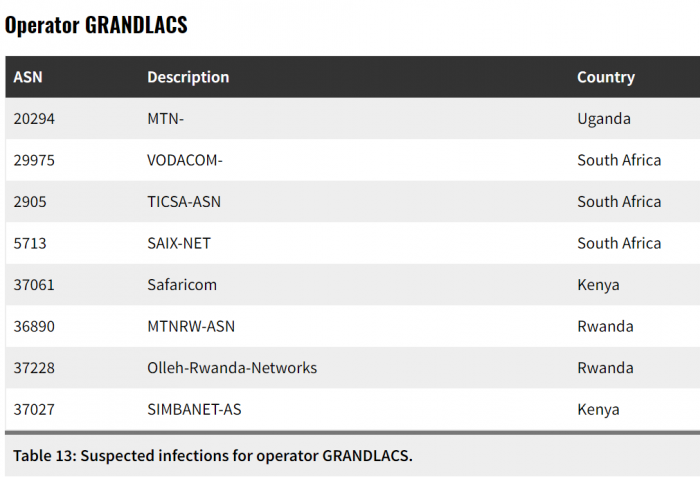

In Kenya, GRANDLACS seems to have targeted users on Safaricom and an enterprise connectivity provider, SimbaNET. There’s little information as to how many people were infected with Pegasus in the country, however, Citizen Lab indicates that GRANDLACS has been active in Kenya since June 2017 to date.
At this point, it is unknown whether the operator, GRANDLACS, has ties to the Kenyan government or this could be external surveillance at play. Citizen Lab does highlight that the use of VPNs could have skewed the correct location of their results.


















