Bitcoin custody options vary in terms of security and control. While custodial platforms like exchanges and ETFs offer convenience, they relinquish ownership and control of Bitcoin to third parties, exposing users to potential risks such as hacking, mismanagement, or regulatory interference. These risks have already had jarring effects with Sam Bankman-Fried of FTX getting a 25-year sentence for fraud.
Self-custodial Bitcoin Wallets
So, what’s the other side of this conversation? Self-custodial wallets offer complete control over your Bitcoin. Unlike custodial solutions, these wallets allow you to independently manage your cryptocurrency without relying on third-party intermediaries. Bitcoin transactions executed through self-custodial wallets are directly between parties, recorded on the blockchain, and resistant to censorship. This is basically, self-sovereignty that gives you full control of your Bitcoin. One such example of self-sovereignty is the Proton Wallet.
“It uses end-to-end encryption (new window) on the keys that control your Bitcoin and your wallet metadata before they’re stored. This means even Proton cannot confiscate your Bitcoin or track your financial activities,” writes Dingchao Lu, Director of engineering at Proton.
Proton does things differently from other types of wallets. For most self-custodial wallets, loss of a device might mean everything you have may be lost forever. However, to ensure reliability, Proton stores encrypted data on its servers and delivers it to users upon successful login.
Furthermore, the platform uses a robust Secure Remote Password (SRP) protocol to authenticate users without storing passwords on its servers, enhancing security. The difference is that many other self-custodial wallets only store data locally.
The wallet employs a robust encryption system to safeguard user data. Passwords are used to encrypt user keys, which are stored on Proton servers. These keys, in turn, encrypt product-specific keys for services like email and wallets.
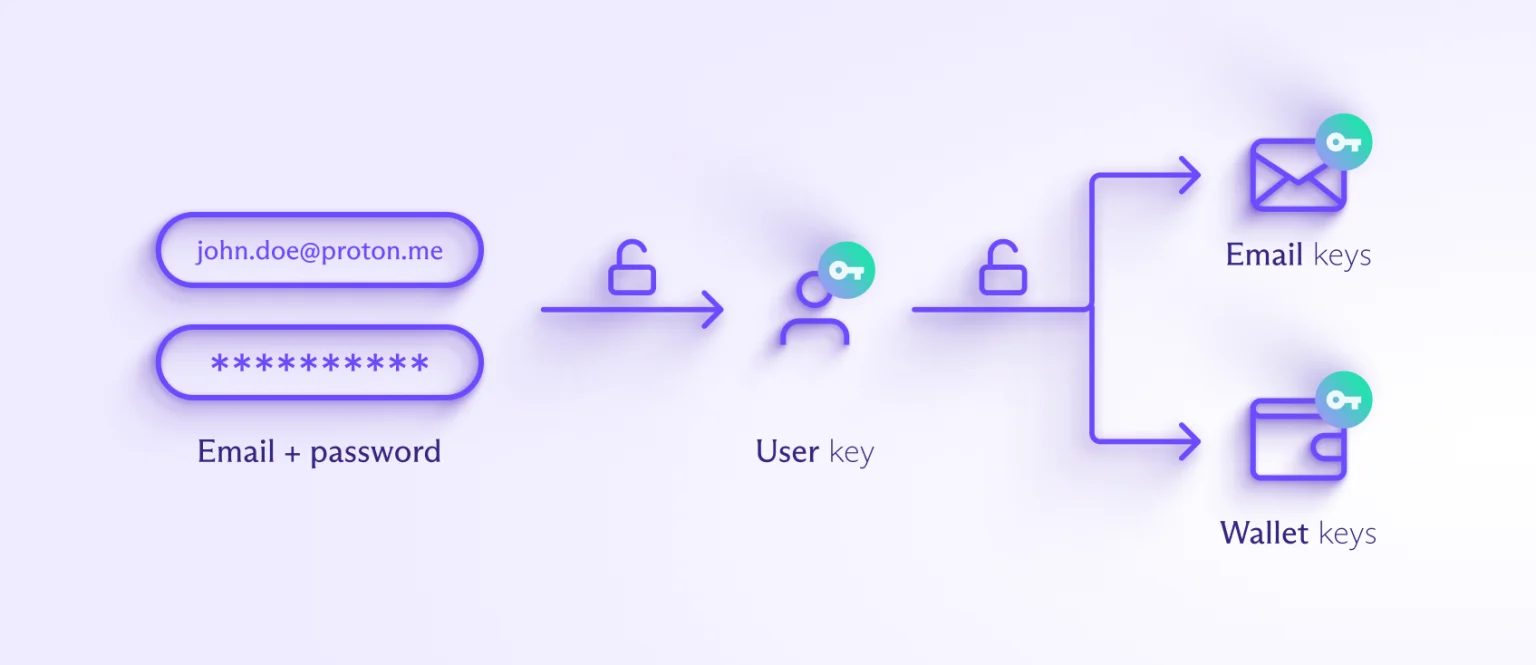
Proton Wallet Data
Sensitive user data, including wallet information, is encrypted on the client device before being stored on Proton’s servers. This ensures that only the user, possessing the correct decryption key, can access their data. Proton Wallet further enhances security by allowing users to create multiple wallets, each protected by its own unique encryption key.
Proton wallets have the following characteristics:
- Wallet Structure: Users can create multiple wallets, each with unique names and Bitcoin addresses. These details, along with wallet seed phrases, are encrypted before storage.
- Seed Phrase Management: The crucial seed phrase, essential for wallet recovery, is encrypted on the user’s device and never stored on Proton servers.
- Data Encryption: Sensitive information, including wallet keys and transaction metadata, is encrypted end-to-end, ensuring protection from unauthorized access.
- Minimal Data Retention: Proton Wallet avoids storing transaction history, balances, or specific Bitcoin addresses on its servers to enhance user privacy.
- Bitcoin via Email: This feature leverages Pretty Good Privacy (PGP) encryption for secure email-based Bitcoin transactions, with minimal data retained by Proton.
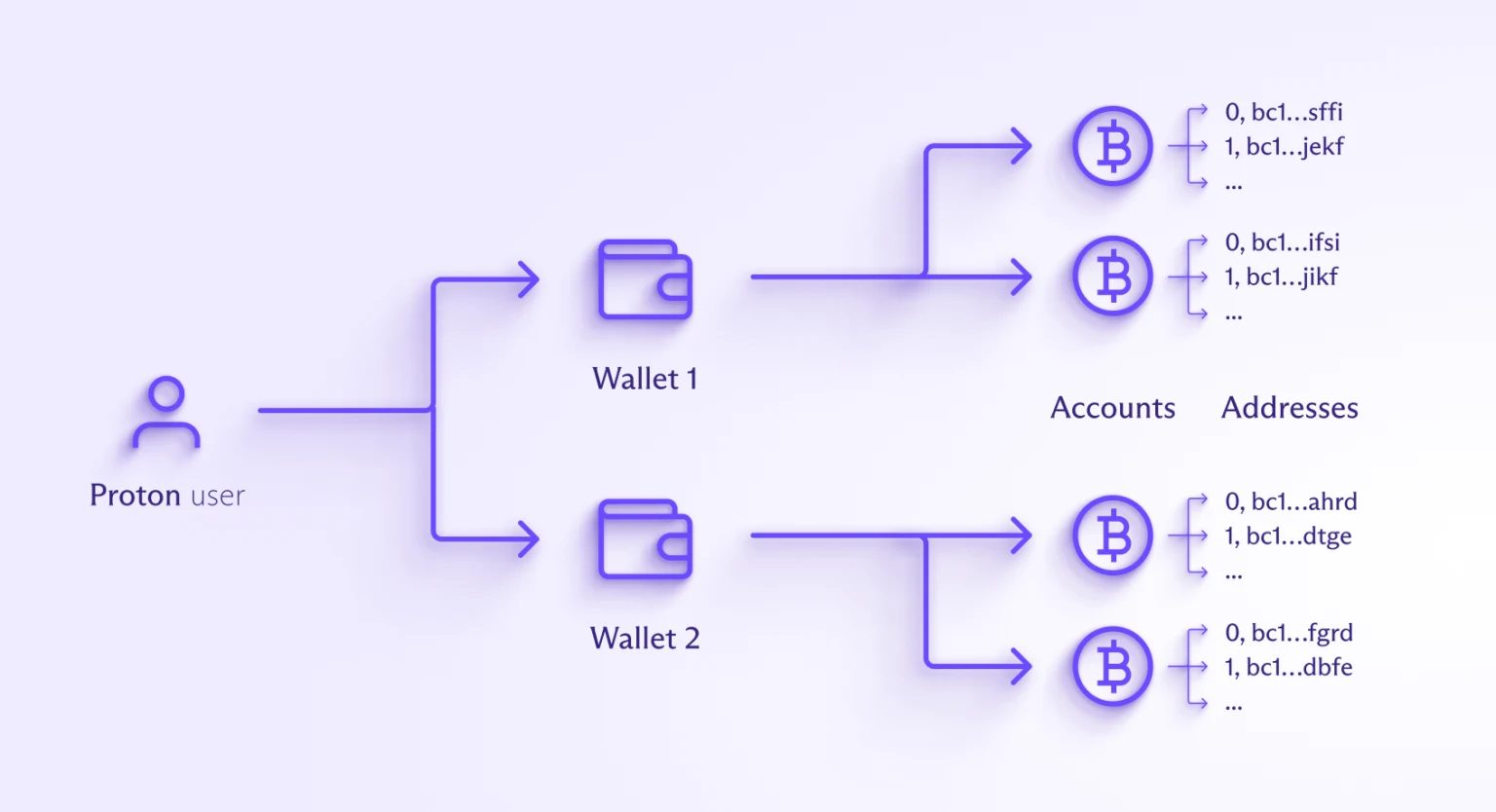
Proton Bitcoin Via Email Feature
Another difference in the Proton self-custodial Wallet is the Bitcoin via Email feature. The usual method for receiving Bitcoin requires generating a public address and sharing it with the sender. This manual process is prone to errors and compromises user privacy, as public addresses can be tracked on the blockchain. To enhance security, users were advised to generate a new address for each transaction.
To simplify the Bitcoin payment process, many individuals use a single address for all incoming transactions. However, this practice compromises privacy as public blockchain records reveal transaction history, including the source and destination of funds.
The unique feature built into Proton Wallet is sending Bitcoin to an email address in a low-friction, private way without reusing Bitcoin addresses. This uses the Proton Mail encrypted email system that has been serving over 100 million accounts since 2014.
Proton Wallet: Sending and Receiving Bitcoin via Email
Proton Wallet offers a unique way to send and receive Bitcoin using email addresses:
1. Setting Up Proton Wallet:
- A user signs up for Proton Wallet using their existing email address (e.g., [email protected]). Verifying ownership of the email is required.
- Alternatively, users can leverage a Proton Mail address for enhanced privacy.
- The user’s Proton Wallet app generates a PGP key linked to their chosen email address for secure communication.
2. Generating Bitcoin Addresses:
- Proton Wallet automatically creates a pool of Bitcoin addresses associated with the user’s main wallet account.
- These addresses are signed with the user’s PGP private key, ensuring only the user can access them.
- The signed addresses are stored on Proton’s servers for functionality.
3. Sending Bitcoin via Email:
- A sender (e.g., Client2 with email [email address removed]) initiates a Bitcoin transaction through their Proton Wallet app.
- The app requests a unique, unused Bitcoin address from the recipient’s ([email protected]) pool stored on Proton’s servers.
4. Verifying Address Authenticity:
- Client2’s app receives the requested address along with a digital signature.
- This signature is verified using the recipient’s public PGP key, ensuring the address originated from Proton’s servers.
5. Sending Encrypted Message and Bitcoin (Optional):
- Client2 can send Bitcoin to the provided address and include an optional encrypted message using the recipient’s PGP public key.
- Only the recipient (with their private key) can decrypt and read the message.
6. Maintaining Privacy:
- Proton Wallet generates a fresh Bitcoin address for each transaction, preventing anyone from linking past and future transactions.
- Attackers cannot learn about a user’s previous transactions by attempting to send Bitcoin, as they’ll receive a different address.
Note: While users must trust Proton to provide the correct public key during address verification, future security features like Trusted Key and Key Transparency aim to minimize this trust.
Wallet Self-Recovery
Proton Wallet is a self-custodial wallet, meaning you have complete control over your Bitcoin. Your private keys, which are essential for accessing your funds, are encrypted and stored exclusively on your device. Proton never has access to them. This paradigm places the primary responsibility for security and asset management on the user.
To safeguard your assets, it is imperative to securely store your recovery phrase, as this is the sole method for restoring access to your wallet in the event of password loss or compromised device. While Proton offers additional security features such as two-factor authentication and account protection, the ultimate responsibility for asset protection lies with the user.
Proton strongly recommend implementing robust security practices, including the use of strong, unique passwords, avoiding phishing attempts, and regularly updating device software.
By understanding these principles and taking proactive steps to protect your account, you can significantly enhance the security of your digital assets.
To recover your wallet in case of lost access, you’ll need your 12-word seed phrase. It’s crucial to securely back this up as it’s the only way to restore your wallet.
For added security, you can set an optional passphrase, but remember, Proton cannot recover this for you if forgotten.
Protecting Your Proton Wallet: Understanding the Risks
Account Compromise The primary threat to Proton Wallet security is unauthorized account access. This typically occurs through phishing attacks or password reuse. Once an attacker gains access, they can potentially view your wallet seed phrase and transfer funds. To mitigate this risk, enable two-factor authentication, use strong, unique passwords, and exercise caution with suspicious emails or links.
Device Compromise If your device is compromised, an attacker can potentially access your Proton Wallet app and steal your information. It’s essential to protect your device with strong passwords, up-to-date software, and caution when downloading files.
Blockchain Privacy While Proton Wallet takes steps to protect user privacy, the public nature of the Bitcoin blockchain means transaction history can be traced. To enhance privacy, consider using tools like coinjoin services.
Proton’s Security Measures Proton employs various security measures to protect user accounts and funds, including advanced phishing filters, account protection programs, and password managers. However, users must also take proactive steps to safeguard their information.
Additional Considerations:
- Backup Your Seed Phrase: This is crucial for recovering your wallet in case of lost or compromised access.
- Beware of Phishing: Be cautious of emails or messages requesting personal information.
- Strong Passwords: Use complex, unique passwords for all online accounts.
- Two-Factor Authentication: Enable 2FA for added security.
- Regular Updates: Keep your device’s operating system and apps up-to-date with the latest security patches.
By understanding these risks and implementing best practices, users can significantly enhance the security of their Proton Wallet and Bitcoin holdings.
Inaccessible Proton Wallet
Unforeseen circumstances, such as internet censorship or service disruptions, may impact access to your wallet. In the event of internet censorship or service outages, Proton VPN can help bypass restrictions and restore access to Proton Wallet. If VPN access is unavailable, your 12-word seed phrase is the ultimate key to recovering your Bitcoin on any compatible wallet. While this process requires manually restoring your wallet and may result in the loss of non-cryptographic data, your Bitcoin assets remain secure and accessible.
It’s essential to prioritize the safekeeping of your seed phrase to ensure uninterrupted access to your funds in any situation
READ: Privacy Changes You Need to Make Right Now
Conclusion
For individuals holding substantial Bitcoin assets, a hardware wallet is often considered the gold standard in security. These devices store cryptographic keys offline, minimizing the risk of digital theft. While Proton Wallet provides robust security features, it’s not designed to replace hardware wallets for those managing significant holdings. Instead, self custody wallets can serve as a secure and convenient complement for everyday transactions.