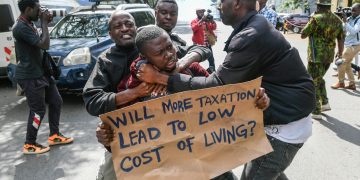Protests are a fundamental right in democratic societies, but in Kenya, as we’ve witnessed lately, exercising this right can put your life at risk. This should not be the case, but unfortunately, we’ve learned very painful and bloody lessons to ignore this fact.
We can write all the tech reviews and opinions we want, but if we’re not helping you, our dear readers, learn how technology can make your life not only simpler but SAFER, we have failed.
That said, we decided to create a detailed guide on how you can use the tech available to you to keep you (and your loved ones) safe during maandamano.
We’ve made it as simple as possible by creating bullet points instead of a whole essay (we’re very aware of the effect TikTok has had on our attention spans).
A lot of our focus will be on smartphones. Though they’re very powerful devices for documenting and organizing, they can also become a liability if you fail to secure them properly.
Therefore, without further ado, here’s a complete guide on how to secure your phone (and yourself) during protests while making your voice heard.
Before You Hit the Streets
Lock Down Your Device
Set Up Bulletproof Encryption
- Enable full-disk encryption to secure your phone immediately before attending any protests
- Create a strong password with 8-12 random characters that you can easily remember and type quickly
- Skip the simple PINs. They’re really not as secure as you think they are
Ditch the Biometrics
- Turn off fingerprint and face unlock features completely
- Police can easily force you to unlock your phone using your face or finger (be it legally or illegally)
- A password in your head is much harder to extract than a finger they can grab
Install Signal for Secure Communication
- Download Signal for end-to-end encrypted messaging and calls
- Set up disappearing messages so conversations don’t remain on your device
- Create group chats with fellow protesters for your own safety. This will help you keep tabs on everyone attending the protests
- Remember: Even secure apps can reveal your location. However, they make it more difficult for people who want to track you
Create Backup Plans for Your Phone
Protect the Data on Your Phone
- Back up everything important before you leave home
- Store backups in a secure location separate from your phone (like a flash drive) before attending protests
- Enable Advanced Data Protection on iCloud if you’re an iPhone user
- Choose zero-knowledge backup services for Android devices
Consider a Burner Phone Strategy
- We know this sounds like something straight out of a movie, but if you can, buy a cheap feature phone (kabambe) – with cash if possible
- Use a temporary number, which you can share with trusted contacts
- Turn off the burner phone before heading home to avoid location correlation
- If you can afford to, dispose of it safely away from your usual locations when done
Dress for Anonymity
Become Invisible in Plain Sight
- Wear dark, monochrome clothes to blend into crowds
- Cover distinctive tattoos, bright hair colors (ladies, please leave those colorful wigs at home), and any other unique features
- Coordinate with your group of friends to dress in a similar fashion
When You’re on the Ground
Master How to Take Photos With Stealth
Document Without Compromising Security
- Use your camera without unlocking your phone (add the camera feature to the lock screen)
- Keep your phone locked and secure as much as possible during the protests
- Consider bringing a separate digital camera for better photo quality (you can bring your DSLR if you feel confident about keeping it safe)
Protect Your Fellow Protesters
- Blur or block out faces of other demonstrators in your photos
- Hide identifying features like unique clothing or accessories
- Use Signal’s built-in blurring tool or dedicated apps like Image Scrubber
Your photos could be used to identify and target others, so be responsible when sharing any form of media.
Strip Away Digital Breadcrumbs
Clean Your Photo Metadata
- Remove location data, timestamps, and device information from images
- Take screenshots of photos to strip metadata quickly
- Send photos to yourself through Signal to automatically remove metadata
- Never EVER post raw photos directly from your camera
Use Public and Private Transport in a Smart Way
Avoid the Digital Paper Trail
- For days such as this, use cash for public transportation instead of linked payment cards like mobile money and cards
- Consider walking (if you can) to avoid license plate readers
- Be aware that your regular car’s plates can be easily tracked using automated systems
- Plan alternative routes home to minimize exposure to surveillance
Control Any Chatter on Your Phone
Go For a Full Communication Blackout
- Enable airplane mode, then manually turn off Wi-Fi and Bluetooth
- Disable all location services completely
- Turn off your phone entirely for maximum protection
- Download offline maps before going for protests
If Things Go Wrong
Know Your Rights During Arrest
- Clearly state that you do not consent to phone searches. Your phone is your property
- Refuse to provide passwords or unlock your device
- Understand that biometric locks can be forced; passwords cannot
- Accept that your phone may be seized, but your consent won’t be
Damage Control After Your Devices Are Confiscated
Cut Off Access Immediately
- Time is both your friend and foe in this situation
- Change passwords for all accounts logged in on your device
- Revoke device access from social media (very important) and other services
- Monitor login logs for unauthorized access
- Consult with a legal advisor before taking any action that might be seen as obstruction
Legal Recovery Options
- Work with a legal advisor to file motions for the return of any devices seized during protests (this only works if you have information on who seized it)
- Understand that devices with potential evidence for illegal activity may be held longer
- Document everything for potential future legal proceedings
Secure Apps and Services To Go For
Essential Security Apps
- Signal for messaging
- Tor browser for anonymous web browsing
- DuckDuckGo for searches that don’t track you or leave browser history
- Avoid Chrome and other data-hungry browsers
Safety on Social Media
- Create separate accounts using anonymous email addresses
- Enable two-factor authentication (2FA) on all accounts
- Consider temporary accounts specifically for protests
- NEVER link protest accounts to your real identity
Advanced Protection Strategies You Can Use
Use Guided Access or App Pinning
- Lock your phone to a single app (consider camera, Signal, or any other app indicated above)
- Prevent unauthorized access to other apps if you need to show your screen to someone
- For iOS: Enable Guided Access in Accessibility settings
- For Android: Use App Pinning in Security settings
VPNs Are Better Than No VPNs
- Choose a paid VPN service over a free one
- Encrypt all your internet traffic
- Hide your real IP address and location
- Set it up before you need it, not during the protests
The Nuclear Option (Or What We Like to Call, “The Best Option”)
Sometimes the best digital security is no digital device at all. Even Snowden can attest to this.
Consider leaving your phone at home entirely if:
- The protests have a chance of being infiltrated by rogue elements (they can undermine all efforts to secure your phone)
- You’re concerned about being specifically targeted
- The risk of losing your devices is high (and it’s not a price you’re willing to pay)
Coordinate with friends beforehand about where to meet and timing if you’re going phone-free.
Our Final Word to You
Please remember that security isn’t about making the perfect safeguards. It’s more about making yourself a harder target than the person next to you. Every precaution you take raises the bar for anyone trying to access your information and data or track your activities.
The most important thing to keep in mind is that these tools and techniques are only as good as your commitment to using them consistently. Practice how to do these steps before you need them, stay informed about new threats and protections, and always prioritize the safety of yourself and fellow protesters.
Your right to protest is fundamental, but being safe while doing so requires preparation, vigilance, and making the right decisions. We have done our part to inform. Now, it’s up to you!