Cubot devices have been in the country for a while now and they seem to be capturing the love of many Kenyans due to their affordable nature and highly packed specifications that the smartphones boast about. Well, the issue at hand does not only affect Kenyans but the world at large. Over the past one year, some Cubot users have noticed a couple of developments with their phones, they have reported that after around two months of usage, the phone starts displaying full-screen ads when one opens certain apps such as WhatsApp, Facebook, Google Chrome and the Play Store.
Cubot devices have been in the country for a while now and they seem to be capturing the love of many Kenyans due to their affordable nature and highly packed specifications that the smartphones boast about. Well, the issue at hand does not only affect Kenyans but the world at large. Over the past one year, some Cubot users have noticed a couple of developments with their phones, they have reported that after around two months of usage, the phone starts displaying full-screen ads when one opens certain apps such as WhatsApp, Facebook, Google Chrome and the Play Store.
Over the past one year, some Cubot users have noticed a couple of developments with their phones, they have reported that after around two months of usage, the phone starts displaying full-screen ads when one opens certain apps such as WhatsApp, Facebook, Google Chrome and the Play Store. The issue has been reported in some of the most common Cubot smartphones such as Cubot Rainbow, Cheetah 2 and Note S.
A user went to Malwarebytes forums and shared his experience. The user discovered that a malware has been embedded within the System UI package of his Cubot Rainbow device.

The malware is said to be trying to connect to the internet a couple of times every minute. After digging deeper, he discovered that System UI accesses an Amazon Web Service (AWS) instance; sdk.asense.in. A domain lookup shows that the said domain belongs to Inter Police, an organization based in Shanghai China.

The malware seems to be the one showing the pop-up ads when you open specific apps, similar complaints have been made through Cubot’s forums. To fix this issue, Cubot released updates for the Rainbow, Cheetah 2 and Note S devices. This update was said to offer “Enhanced protection against malware”, and for a while, it seemed like it did, as the System UI apk file got a 0/56 virustotal score.

However, it was discovered that Cubot had removed the malware from the System UI package and hidden it under a new package, com.android.telephone, disguised as the phone dialer. On further digging, it was discovered that the new package does not have any real function and it manages to evade any detection by antivirus apps such as NetGuard, that would detect the malware under System UI previously.
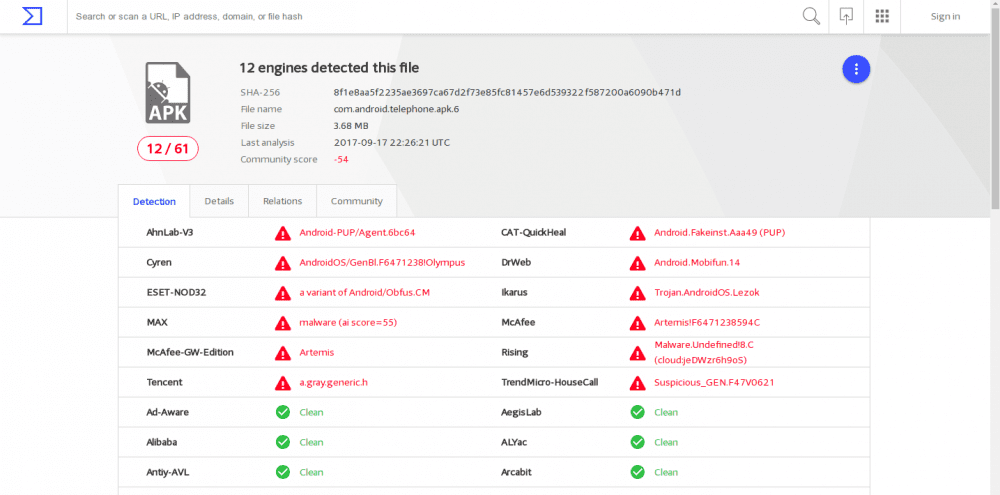
The new package aggressively pings Cubot’s Amazon-based servers (sp2.l1181.com), causing a lot of battery drain and unexplainable data consumption. The app also constantly gives itself permission to read and write your storage every 2 seconds or so. Things get worse for Cubot users as this app cannot be disabled, permissions cannot be changed and if the phone is reset to factory defaults, the malware reactivates after some time.
We also discovered that another system application on Cubot’s software has been accused of being a spyware. The wireless update app Cubot uses is provided by ADUPS, an app that has been reported to have serious security issues. The Wireless Update app can install unwanted Apps silently, execute remote commands and transmit personally identifiable information without user consent or disclosure.
The only way to protect yourself from getting these pop-up full-screen ads and preventing your data from being mined is by blocking the Wireless Update app and the com.android.telephone app from accessing internet connection through the phone’s settings or by using a third-party firewall app such as NetGuard.
We reached out to Cubot for a comment on these findings and accusations and at the time of publishing, the company had not yet responded to our questions. The irony of this whole discovery is that the company’s tagline translates to “Simple & Trustworthy.”
UPDATE:
Cubot replied to our questions and made a stand that the company does not include malware in their devices. The reply was rather cut and dried but we got the message:
As for this issue, I confirm we don’t include malware within our software. Since your phone has been connected to a network or wifi all the time, also downloading software from different websites, this can be the cause of the malware.